 Described by the MPA, Premier League and other rightsholders as a priority piracy threat, a set-top box available to buy right now on popular markets, initially sounds like an attractive buy.
Described by the MPA, Premier League and other rightsholders as a priority piracy threat, a set-top box available to buy right now on popular markets, initially sounds like an attractive buy.
Manufactured in China, EVPAD TV boxes look fairly unremarkable, and with an Android 7.0 operating system under the hood, they are. When purchased with a cheap ‘lifetime’ subscription, with installable apps providing access to all the content most people will ever need, looks become less important.
However, a look under the hood reveals that the trade-off between content and privacy cannot be ignored.
Researchers Investigate EVPAD
Android-based EVPAD devices provide access to a huge library of infringing movies, TV shows, and live TV, sourced from countries including Canada, Taiwan, the UK, and the United States, among others. As a result, major rightsholders have regularly reported EVPAD and similar devices to the USTR’s Notorious Markets review.
A team of researchers at Korea University took an interest in the EVPAD ‘3p’ and ’10p’ devices when considering what type of anti-piracy measures might be effective against device-specific apps, operating within closed, subscription-based networks.
In this case, the EVPAD website advises buyers of the ‘3p’ device to download two apps from a third party website. ‘StarLive’ and ‘StarVod’ provide access to live TV broadcasts and VOD content, respectively. For the ’10p’ device, a single app called ‘StarV10’ is sufficient and in all cases, installation is simplicity itself.
 “Interestingly, during the installation process from such unknown sources, the service applications are installed seamlessly without requiring any additional user interaction or explicit permissions,” the researchers report.
“Interestingly, during the installation process from such unknown sources, the service applications are installed seamlessly without requiring any additional user interaction or explicit permissions,” the researchers report.
“Upon further inspection, we found that the global system setting for package installation from non-market sources (install_non_market_apps) was set to 1, indicating that side-loading from unknown sources is universally permitted on this Android 7-based device.”
For regular buyers, zero control over permissions should’ve been an immediate red flag. For the researchers, the secrets of obfuscated source code were still to be discovered.
“Streaming is Safer Than Torrents”
Since regular streaming is a process of consumption and the law tends to view supply more seriously, the theory that streaming is safer than torrents usually finds solid ground.
That doesn’t necessarily mean that streaming pirated content is legal, but in a client/server streaming scenario, obtaining evidence of downloading meets technical challenges that aren’t easily overcome. In contrast, BitTorrent users upload by default, which makes evidence of a more serious offense comparatively easy to obtain.
When people buy an EVPAD TV box, many will expect to ‘stream’ pirated content to the device. While that may be a part of the process, the reality is less straightforward.
A Hybrid Network
The researchers at Korea University found that EVPAD devices initially communicate with centralized servers, which manage authentication, various updates, and the all-important content lists. Once obtained, EVPAD devices use that information to join a BitTorrent-like peer-to-peer (P2P) network, in which unwitting downloaders become simultaneous uploaders, or as they say in court, unlicensed distributors of infringing content.
StarLive uses the ‘libtvcore‘ library to establish connections with other EVPAD devices, enabling real-time data sharing among peers, including the distribution of live TV broadcasts.
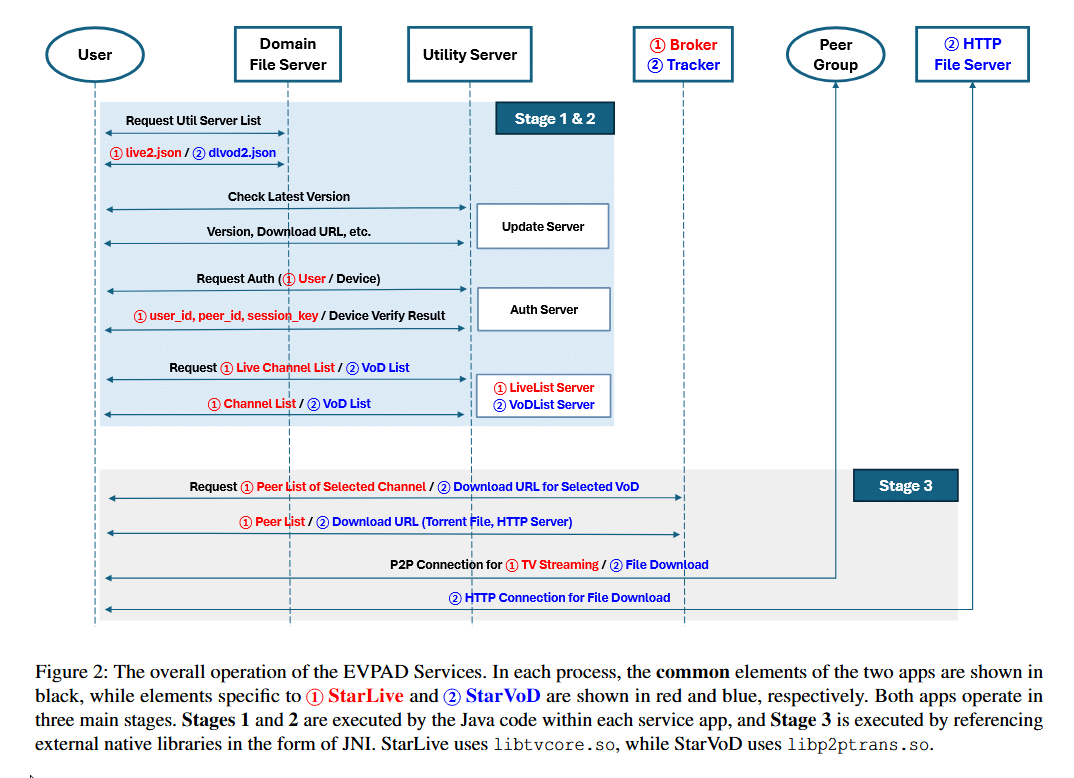
When a user of StarVod selects a video to watch, the system identifies a corresponding .torrent file and HTTP file server. Encrypted using XOR, the .torrent file is decrypted by the libp2ptrans library then used to perform standard BitTorrent functions, with a tracker providing a list of available peers.
“Simultaneously, the user engages in both P2P communication with other peers and HTTP communication with the file server delivering the selected VoD title. This dual approach ensures both downloading and streaming, but in practice, HTTP streaming via a dedicated file server significantly enhances service availability and playback speed, often playing a major role in video streaming,” the researchers note.
Hybrid Network Complicates Blocking
This hybrid approach to networking complicates blocking efforts. While blocking certain domains would prevent service updates, that may not necessarily disrupt the P2P network.
In the event that the source of content becomes unavailable, the researchers say that data broadcasting nodes in the P2P network provide a fallback mechanism by acting as servers within the ‘swarm’. For video-on-demand (VoD) content, the system utilizes P2P but when necessary, HTTP is used to reach servers operating as Content Delivery Networks.
“[These servers] distribute torrent files and video content, and the presence of multiple similar domains suggests that they are designed to quickly circumvent domain blocks. Additionally, there are domains and IP addresses for Trackers to facilitate torrent-based communication,” the researchers add.
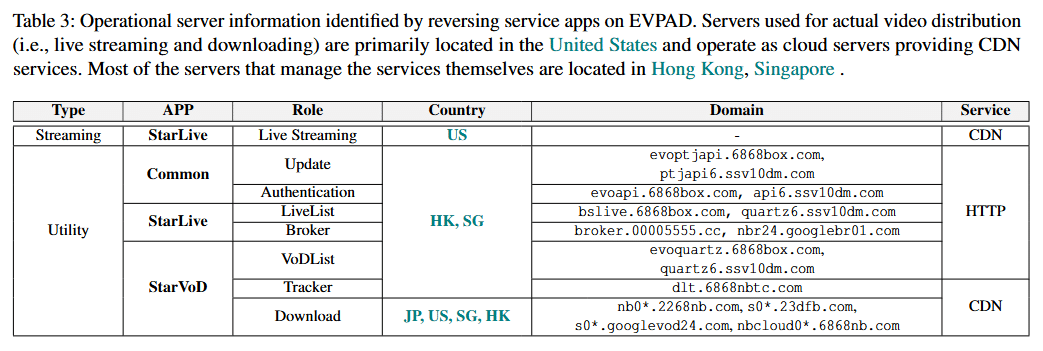
After manipulating IDs used to identify content categories, the researchers obtained all VOD lists from the servers above, which together identified 24,934 pieces of video content. That included 1,052 movies and TV shows in the ‘Nflix’ category alone.
Building Resilience Introduced Weakness
No system is completely bulletproof, and this one is no exception. In theory, the decentralized nature of the P2P network makes the system more difficult to shut down. In practice, it also introduces vulnerabilities that can be exploited to disrupt the service.
The researchers discovered two vulnerabilities. Using the Android emulator NoxPlayer to mimic an authenticated EVPAD device, the first allowed them to bypass authentication. This enabled content to be viewed from around the world, without a subscription, with the potential for “unlimited replication.”
While the first vulnerability granted access to the network, the second vulnerability instantly denied it.
“Given the critical nature of this vulnerability, we determined that even a single, carefully crafted TCP packet is sufficient for an individual to trigger service termination on a remote peer device. This drastically lowers the bar for potential abuse, as no significant bandwidth or coordinated effort is required,” the team note.
Blocking Measures Disrupt the EVPAD Network
When combined, these vulnerabilities form the basis of a theoretical anti-piracy strategy. Once a node is deployed in every available TV channel, the data normally used to connect peers can be leveraged for a different purpose. It allows an attacker to identify specific users and hit them with a TCP packet, causing an instant disconnection.
There’s no suggestion that such an attack has ever been used outside a lab environment. However, the researchers mention an injunction obtained in India by the Premier League that granted authority to block certain domains, which caused network disruptions lasting four days.
While service was restored, the researchers say that would’ve been more difficult if additional capability had been deployed alongside.
Implications For End Users
Beyond the inherent risks of sharing copyrighted content, the implications for users of EVPAD devices are significant. Often distributed in a pre-rooted state with no package installation restrictions, EVPAD devices are highly vulnerable to abuse. The researchers found that the device update process lacks any mechanism to verify integrity or authenticity.
The device also operates with SELinux in permissive mode, where policy violations occur without enforcement. These factors and others lead to the conclusion that attackers could secure a global network of “zombie” devices through which they could execute further attacks by remote control.
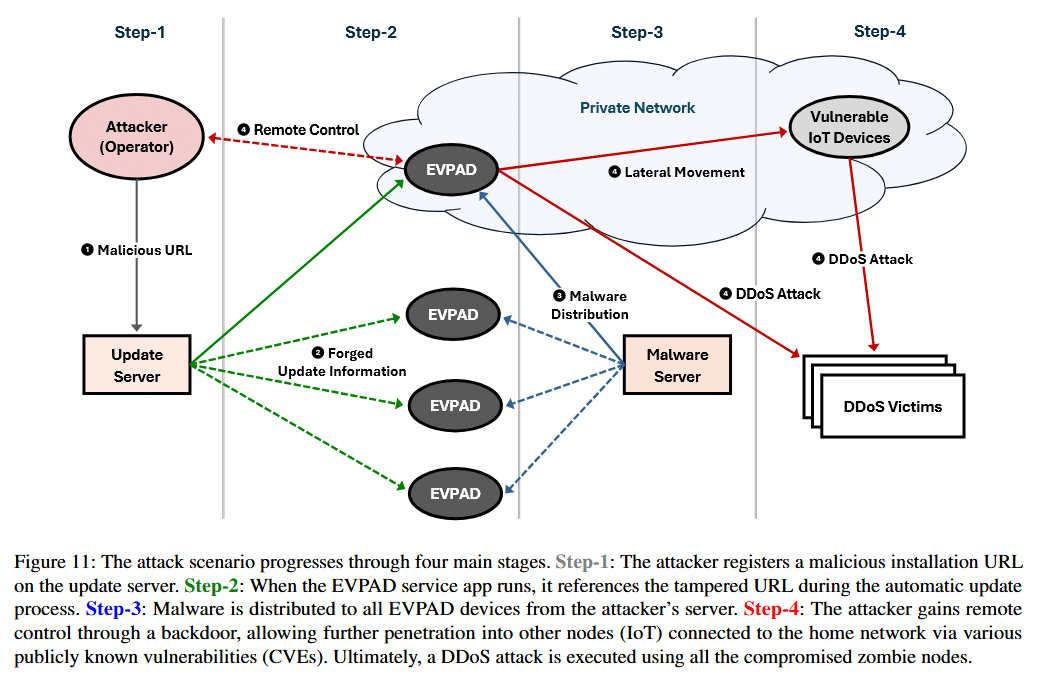
“At its peak, [the Mirai botnet] generated about 1TB of attack traffic using 145,000 devices,” the researchers note, adding that 17,000 compromised EVPAD devices could “potentially generate up to 0.12TB of malicious traffic at peak.”
The study identified 131,175 devices across 116 countries and 78 operational servers located in the United States, Japan, Singapore, Hong Kong, and other countries
“Even if malicious intent is not the primary motive, the lack of commitment to user security by such illegal operators places users in a vulnerable position, making them susceptible to attacks.”
Watch Out Your TV Box: Reversing and Blocking a P2P-based Illegal Streaming Ecosystem, is available here (pdf)
From: TF, for the latest news on copyright battles, piracy and more.
Powered by WPeMatico
