3 key open source challenges in developing countries
3 key open source challenges in developing countries Ahmed Sobeh Thu, 04/27/2023 – 03:00 When I go back home and talk to people in the tech industry, or any other industry for that matter, about what I do and the topics I’m involved in daily, I’m usually met with bemusement at the idea of an Open Source Programs Office (OSPO). The concept of a company contributing to an open source project without obvious immediate...
Test your Drupal website with Cypress
Test your Drupal website with Cypress cobadger Wed, 04/26/2023 – 03:00 If you don’t include tests in your Drupal development, chances are it’s because you think it adds complexity and expense without benefit. Cypress is an open source tool with many benefits: Reliably tests anything that runs in a web browser Works on any web platform (it’s great for testing projects using front-end technologies like React)...
5 open ways to help UX designers and developers collaborate better
5 open ways to help UX designers and developers collaborate better kriker Wed, 04/26/2023 – 03:00 Ideally, designers have a good relationship with their product team and users. However, the relationship between designers and developers is more difficult to build and maintain. The lack of a close relationship makes it difficult to solve problems or improve. In my experience, the open source Open Decision Framework can overcome...
What’s new in GNOME 44?
What’s new in GNOME 44? Jim Hall Tue, 04/25/2023 – 03:00 I use GNOME as my primary desktop environment on my Linux PC at home. GNOME gives me an easy-to-use graphical desktop that provides the flexibility I need yet doesn’t get in my way when I focus on my work. GNOME recently released GNOME 44 with a bunch of new features. I reached out to the GNOME team to ask about the latest version and what was in it....
Retry your Python code until it fails
Retry your Python code until it fails Moshe Zadka Tue, 04/25/2023 – 03:00 Sometimes, a function is called with bad inputs or in a bad program state, so it fails. In languages like Python, this usually results in an exception. But sometimes exceptions are caused by different issues or are transitory. Imagine code that must keep working in the face of caching data being cleaned up. In theory, the code and the cleaner could...
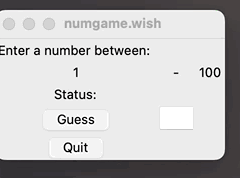
Learn Tcl/Tk and Wish with this simple game
Learn Tcl/Tk and Wish with this simple game JamesF Mon, 04/24/2023 – 03:00 Explore the basic language constructs of Tcl/Tk, which include user input, output, variables, conditional evaluation, simple functions, and basic event driven programming. My path to writing this article started with a desire to make advanced use of Expect which is based on Tcl. Those efforts resulted in these two articles: Learn Tcl by writing a simple...